In today’s digital world, the cloud is an indispensable part of the IT infrastructure for companies of all sizes. More and more services – regardless of industry – are being delivered via the cloud. But while the cloud offers numerous advantages, such as scalability, flexibility and a reduced IT administration effort, it also raises security issues – both for the cloud provider and the using companies. This is why the shared responsibility model is often used in cloud computing. In concrete terms, this means that both parties, the cloud provider and the customer, share responsibility for cloud security.
Short & concise:
- The shared responsibility model regulates responsibility in security matters between the cloud provider and the using companies.
- While the cloud provider is responsible for the security of the cloud, the cloud-using company is responsible for the security of all data in the cloud.
- Identity ans Access Management has established itself as a new, central element for cloud security strategy.
Shared Responsibility – Working together for more security
The shared responsibility model is an important basis for cloud security concepts. It was developed by public cloud providers such as amazon, IBM, etc. to clearly define the responsibilities for security between the provider and the customer. At its core, the model is based on the assumption that the security of data and applications is not the sole responsibility of the cloud providers or the cloud-using companies. All necessary security measures are clearly defined and shared between the two parties – so each partner takes responsibility for their defined area.
Without this partnership model, cloud providers would be entirely responsible for the security of all areas. In the event of a data leak, the provider would not only face a recourse claim from the customer, but would also have to reckon with a loss of reputation in the industry. With the shared responsibility model, an important part of the responsibility, namely data security, is now transferred to the customers. With clearly defined areas of responsibility, cloud providers no longer have to fear being held responsible for their customers’ mistakes. But the cloud-using companies also benefit from the model. Cloud services such as software-as-a-service actively reduce the workload on the data center and require fewer IT staff. In addition, technical functionality is ensured as this is monitored and controlled by the cloud provider. So customers only have to worry about securing the data and the applications, which significantly reduces the workload.
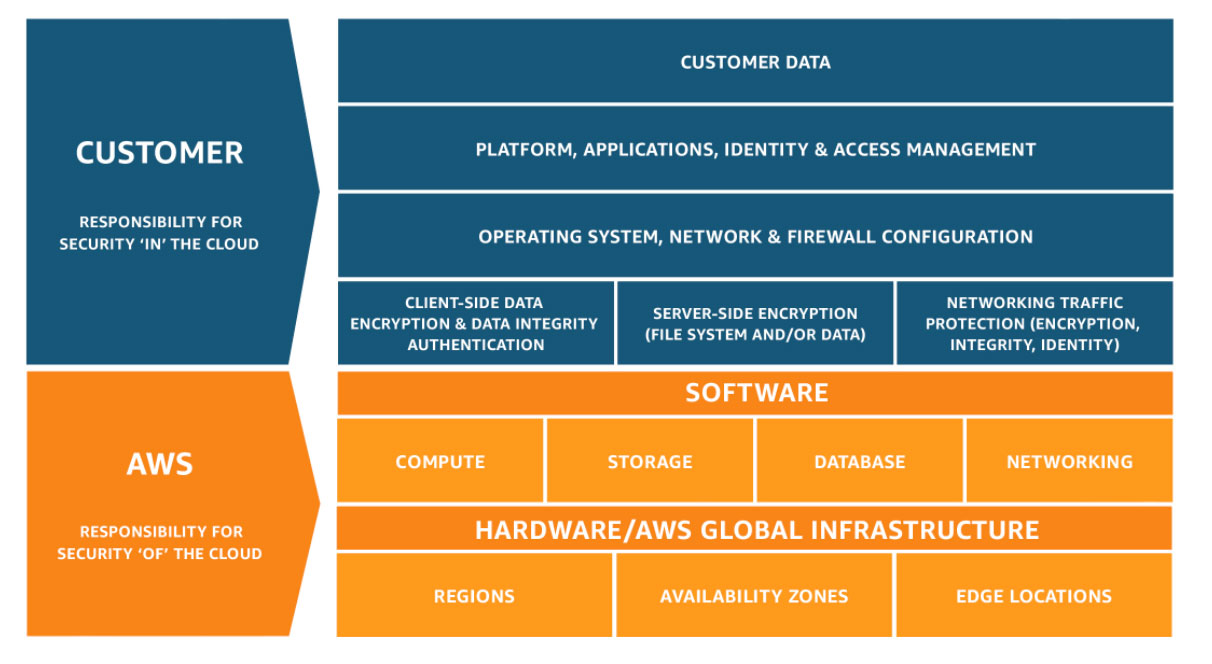
The Shared Responsibility Model as defined by AWS for itself and its customers.
Source: https://aws.amazon.com/compliance/shared-responsibility-model/
The role of the cloud provider
In the Shared Responsibility Model, the cloud provider takes responsibility for the security of the cloud. On the one hand, this includes infrastructure security, which means that he is responsible for the physical security of the data centers and server locations, the securing of the databases and the integrity of the system functions. On the other hand, he ensures the security of the cloud network, including the Internet connection.
In addition, the cloud provider usually offers a range of security services and tools to help users protect their data and applications more effectively. These can be firewall services or encryption options, for example. Cloud providers are also responsible for platform security: this covers the security of the cloud platform itself, including the virtualization layer and the operating system.
Security responsibility of the customers in the cloud
While the cloud provider is responsible for the security of the cloud, customers themselves must ensure security in the cloud. This includes protection of their own data, access to it and associated permissions, and can be achieved using encryption, access controls and security policies. Close monitoring of data activities is also necessary. The cloud provider provides various tools for this purpose. However, it is the user’s responsibility to configure, implement and adequately protect these according to individual requirements.
Access management is also the responsibility of the customers. It includes the management of user accounts, authorizations and passwords and also applies to access from mobile devices. It must be ensured at all times that only authorized users can access the cloud. In addition, customers are required to review and adjust the security configuration of their cloud services to minimize any vulnerabilities. This includes updating software, configuring firewalls and applying security policies. Regular and proactive monitoring of cloud environments is also essential to detect suspicious activity in a timely manner. This enables a rapid response to security incidents, minimizing damage and closing security gaps.
New key element – Identity and Access Management
Currently, a new key element for cloud security strategy has emerged: Identity and Access Management (IAM). It encompasses the management of identities, credentials and access to resources in the cloud and helps organizations improve productivity, information security and data protection in IT.
When using cloud services, companies should consider the following important aspects:
- Identity management: In the cloud, organizations must adhere to strict policies for assigning and managing identities for employees, services and applications. It is important to use multi-factor authentication to protect access to sensitive data.
- Authorization management: It is advisable to keep the allocation of authorizations to a minimum (least privilege). Employees and services should only receive the authorizations they really need for their tasks. These should be regularly reviewed and updated.
- Monitoring and logging: All activities related to identities and access must be strictly monitored and logged. This allows suspicious activities to be identified quickly and appropriate measures to be taken directly.
- Compliance: Companies must ensure that their identity and access management complies with legal requirements and industry-specific standards. This is especially important in regulated industries such as healthcare and financial services.
- Training and awareness: Employees should be trained on IAM policies and procedures and made aware of the importance of security.
The Shared Responsibility Model is an important concept for ensuring cloud security effectively. Companies in particular must be aware of their active role in securing the cloud infrastructure – especially in the area of identity and access management. After all, careful implementation of IAM policies is an important key to minimizing security risks and protecting the cloud environment.